Summary
End-to-end integration of Minecraft anti-cheat telemetry with Wazuh SIEM for real-time X-ray detection monitoring and dashboard visualization.
- Deployed PaperMC server with Sentinel anti-cheat plugin for behavioral monitoring
- Configured Wazuh Agent to collect and forward JSON logs to existing SIEM infrastructure
- Created dedicated Minecraft group and normalized log fields for proper aggregation
- Designed custom visualizations and dashboard for multiplayer server oversight
Start PaperMC server from JAR
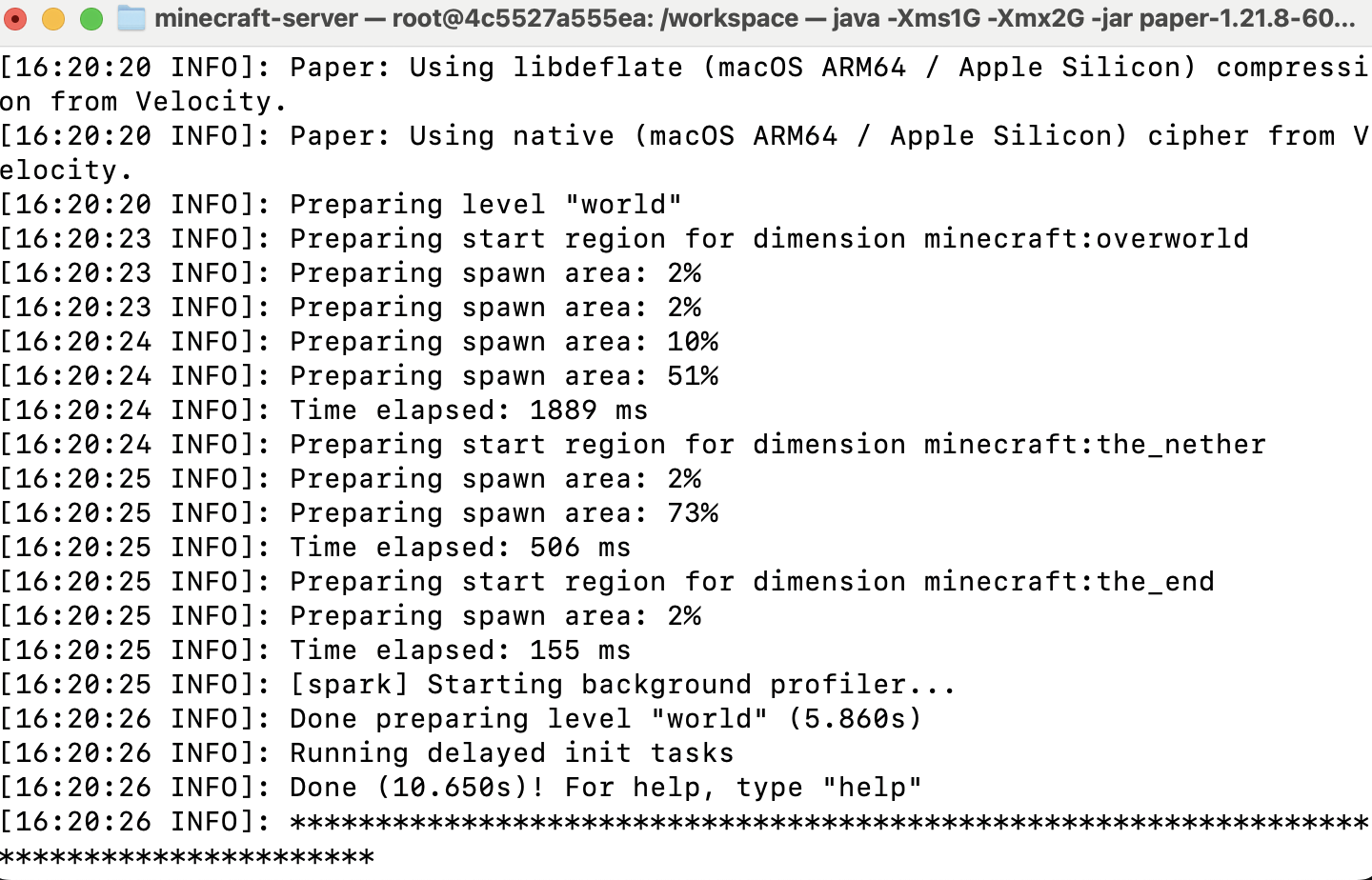
Boot a PaperMC instance locally using the server JAR to host a test world for telemetry.
Build the Sentinel plugin
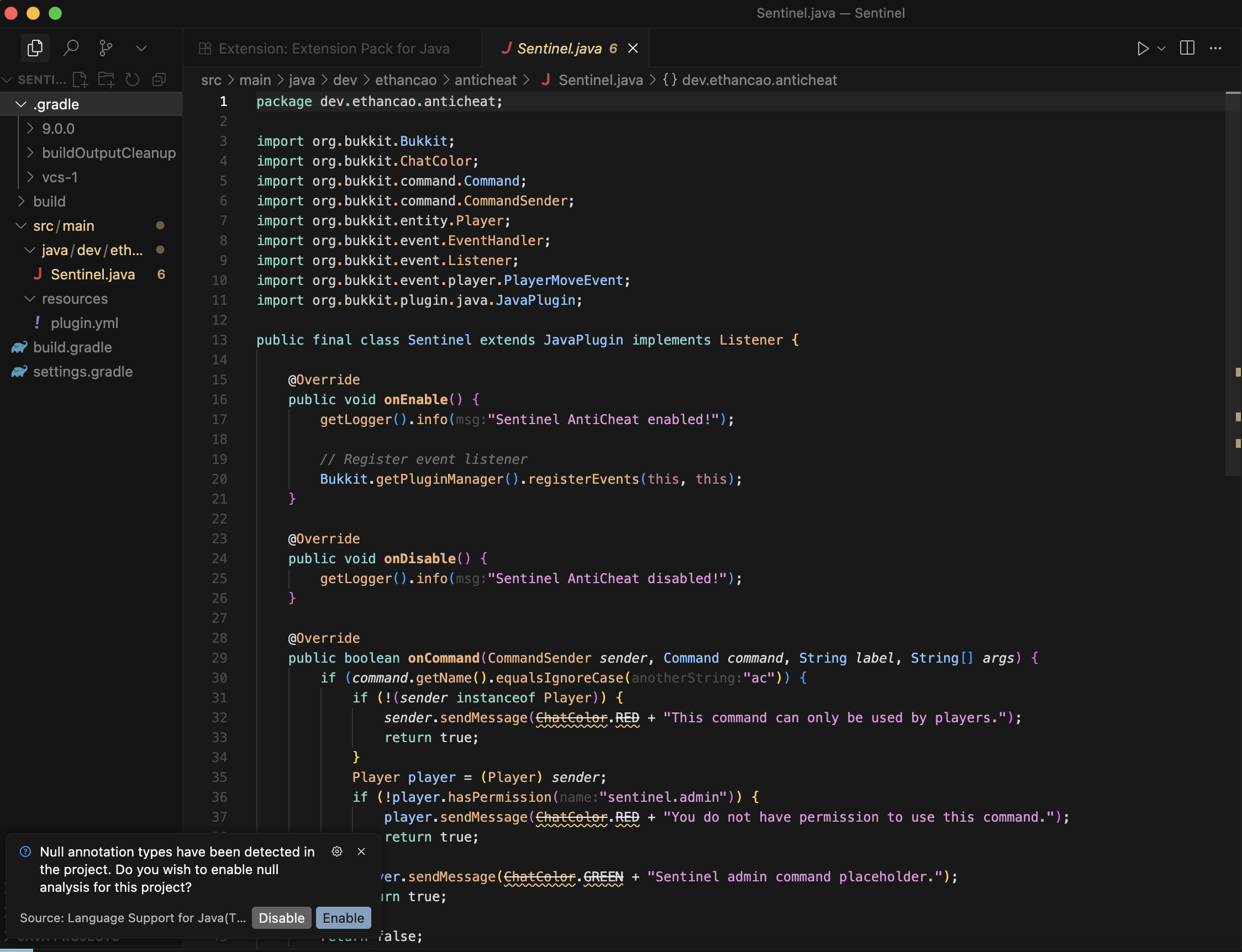
Compile the full Sentinel plugin and prepare the output JAR for deployment on the server.
Load plugin on startup
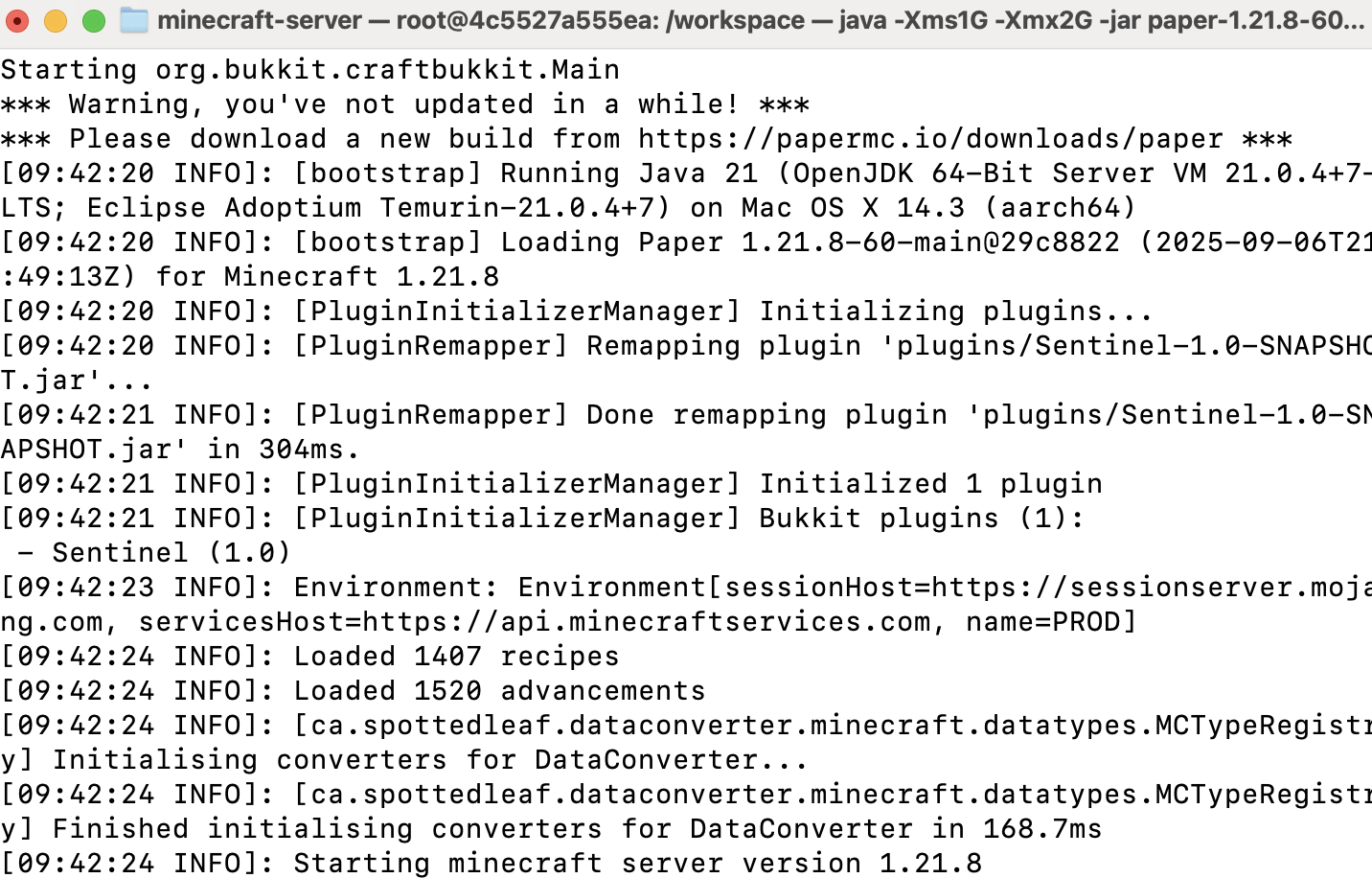
Place the plugin JAR at plugins/sentinelsnapshot.jar; verify it loads cleanly on server start.
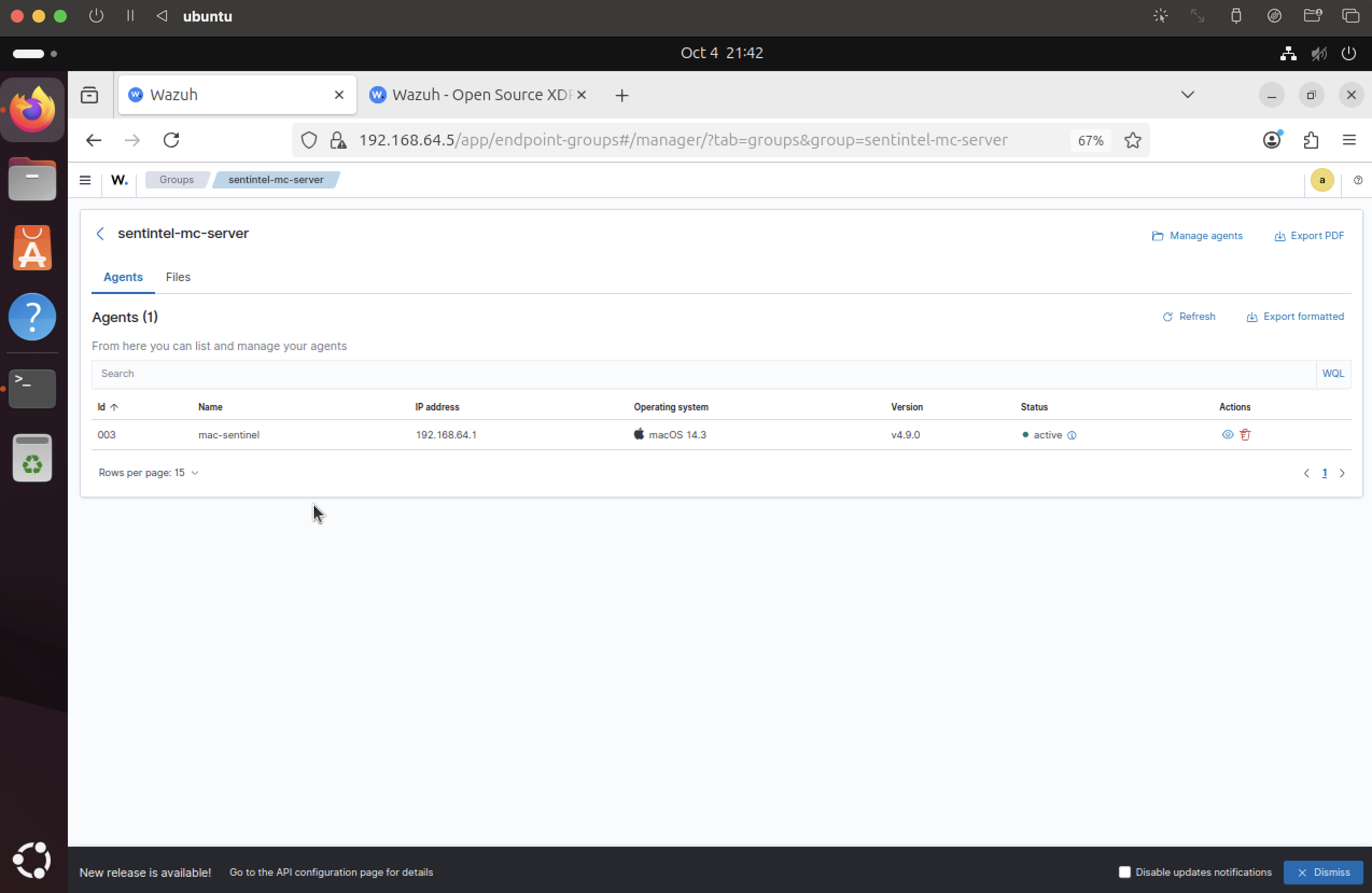
Reuse prior Wazuh server; create Minecraft group
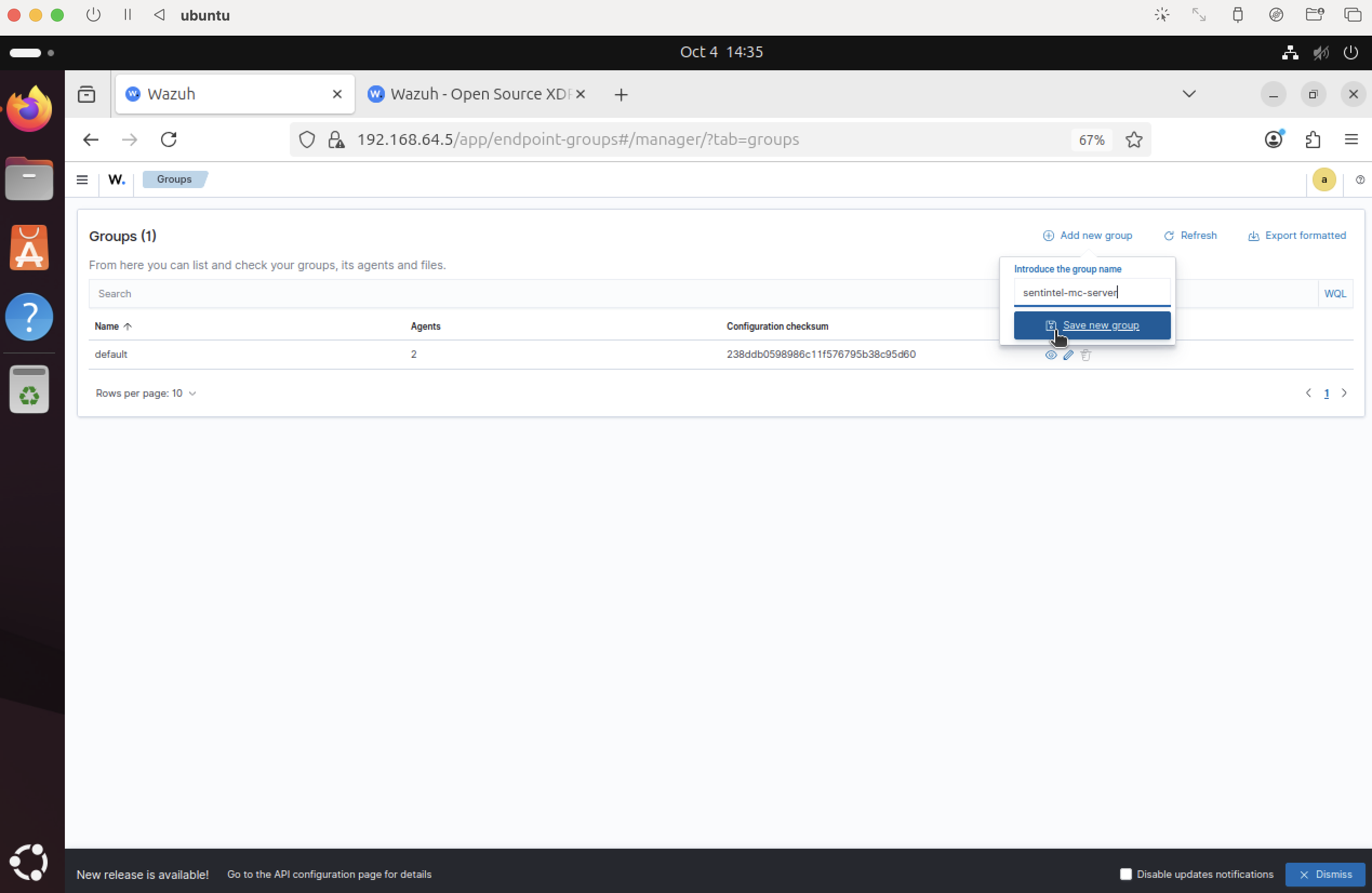
Leverage the existing Wazuh SIEM from a prior lab. Create a dedicated group (e.g., sentinel-mc-server) to isolate Minecraft telemetry.
Install Wazuh Agent on the MC host
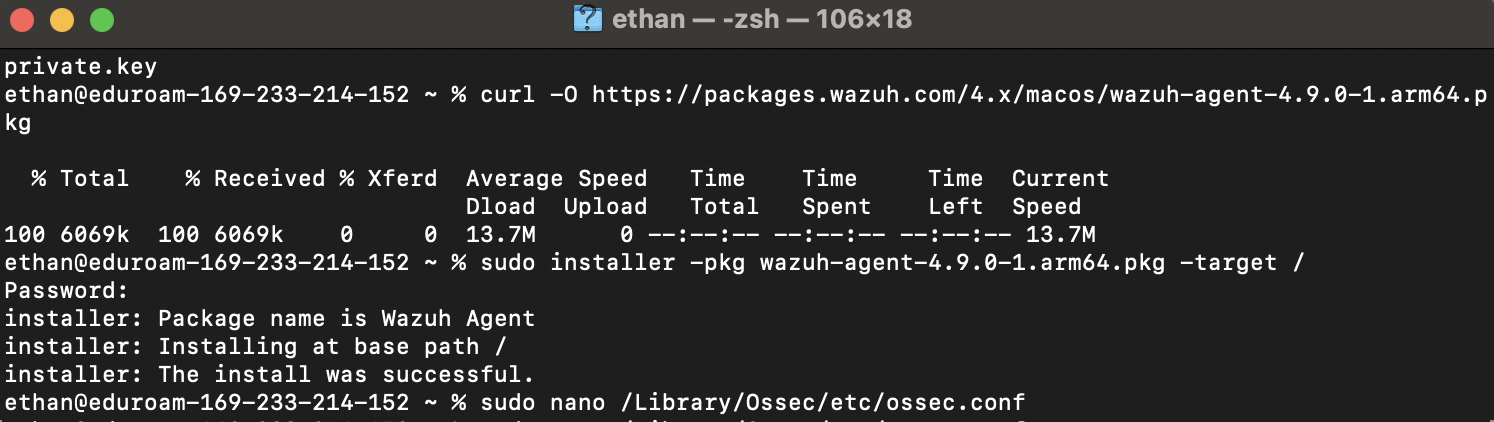
Deploy the agent on the same machine as the server to ship JSON logs produced by Sentinel.
Point agent to correct log file and SIEM IP
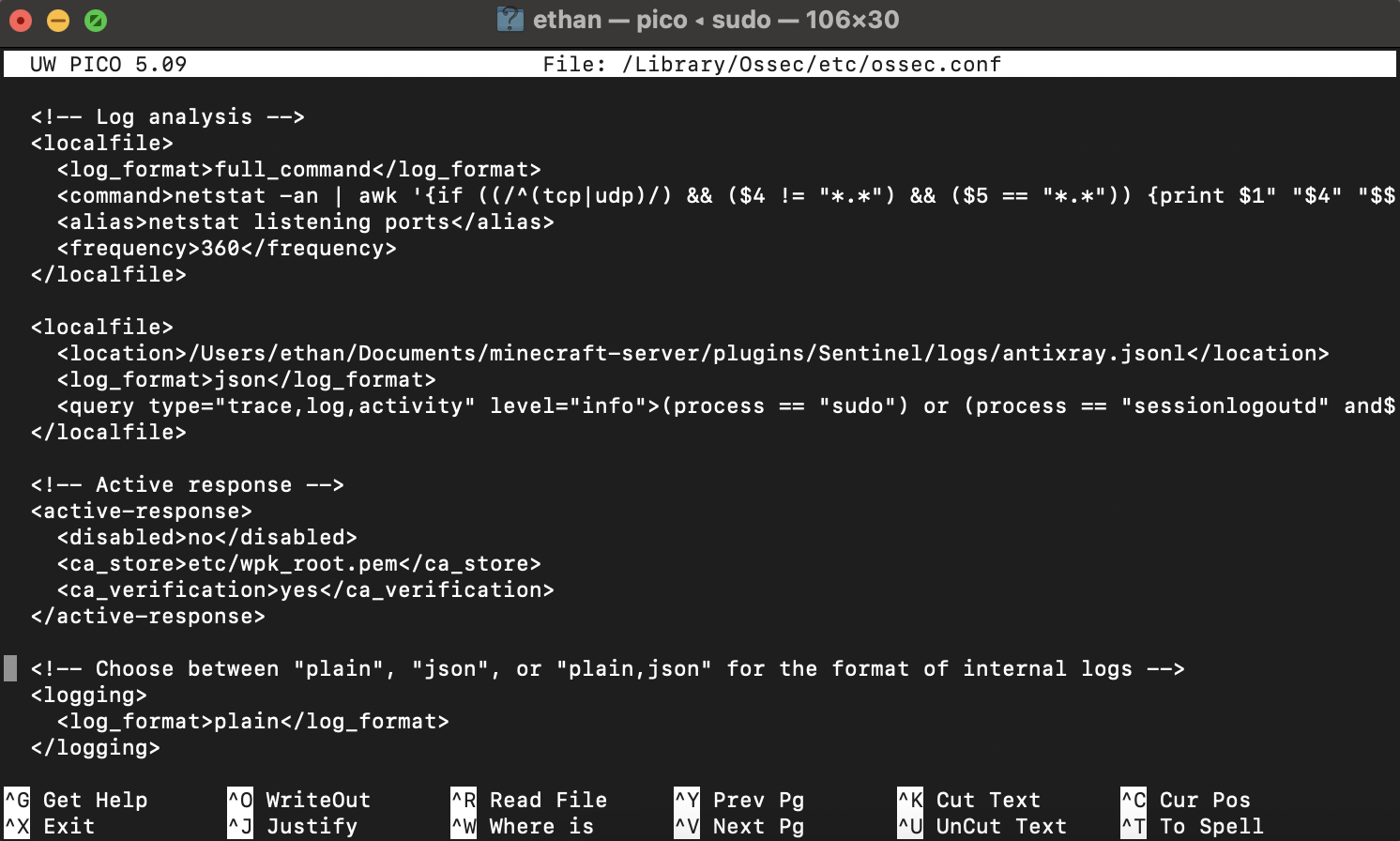
Update the agent configuration to monitor the Sentinel JSON log and forward events to the Wazuh server’s IP.
Register agent with Wazuh
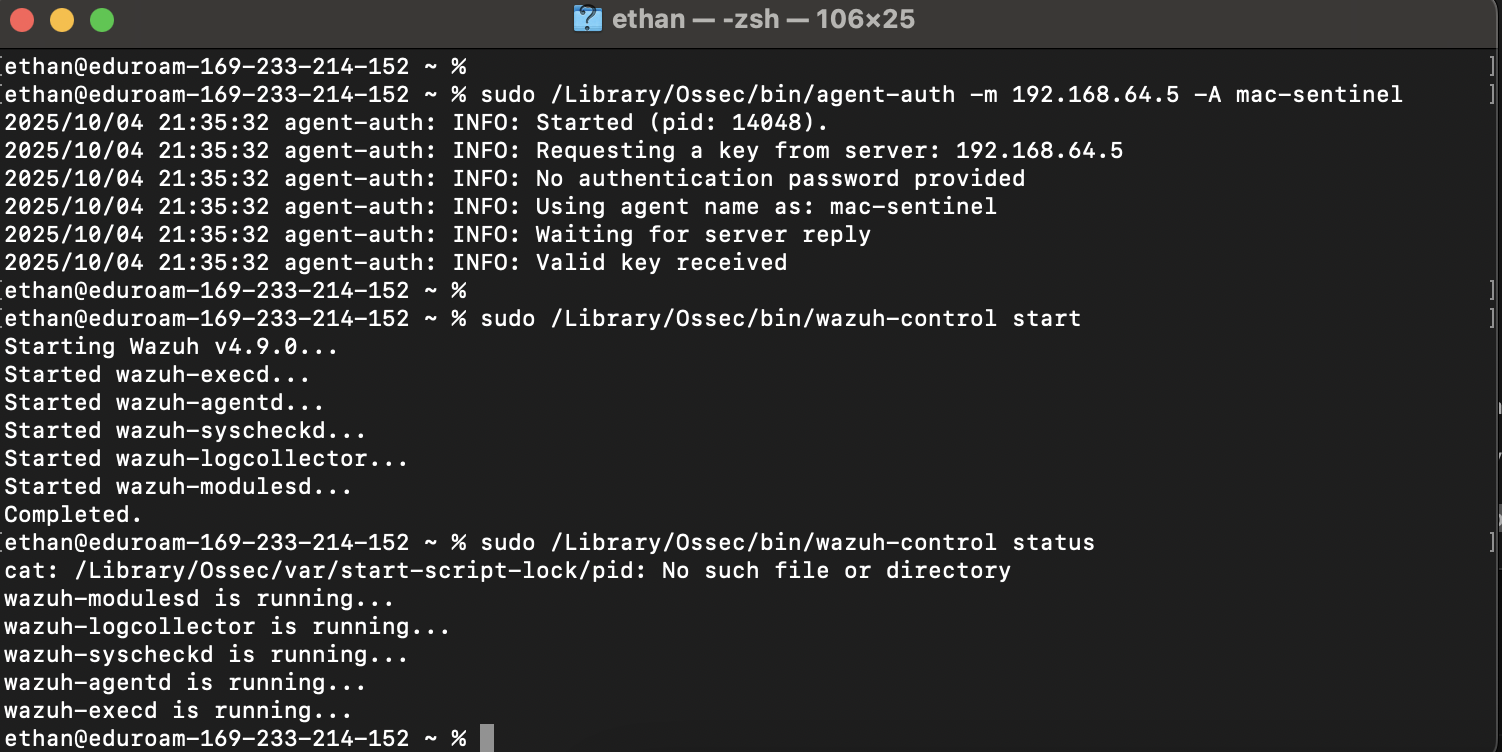
Enroll the host in Wazuh and assign it to the sentinel-mc-server group for policy and views.
Harden agent config; enable JSON log analysis
Disable unnecessary modules and tune log collection to focus on Sentinel’s JSON output for efficient parsing.
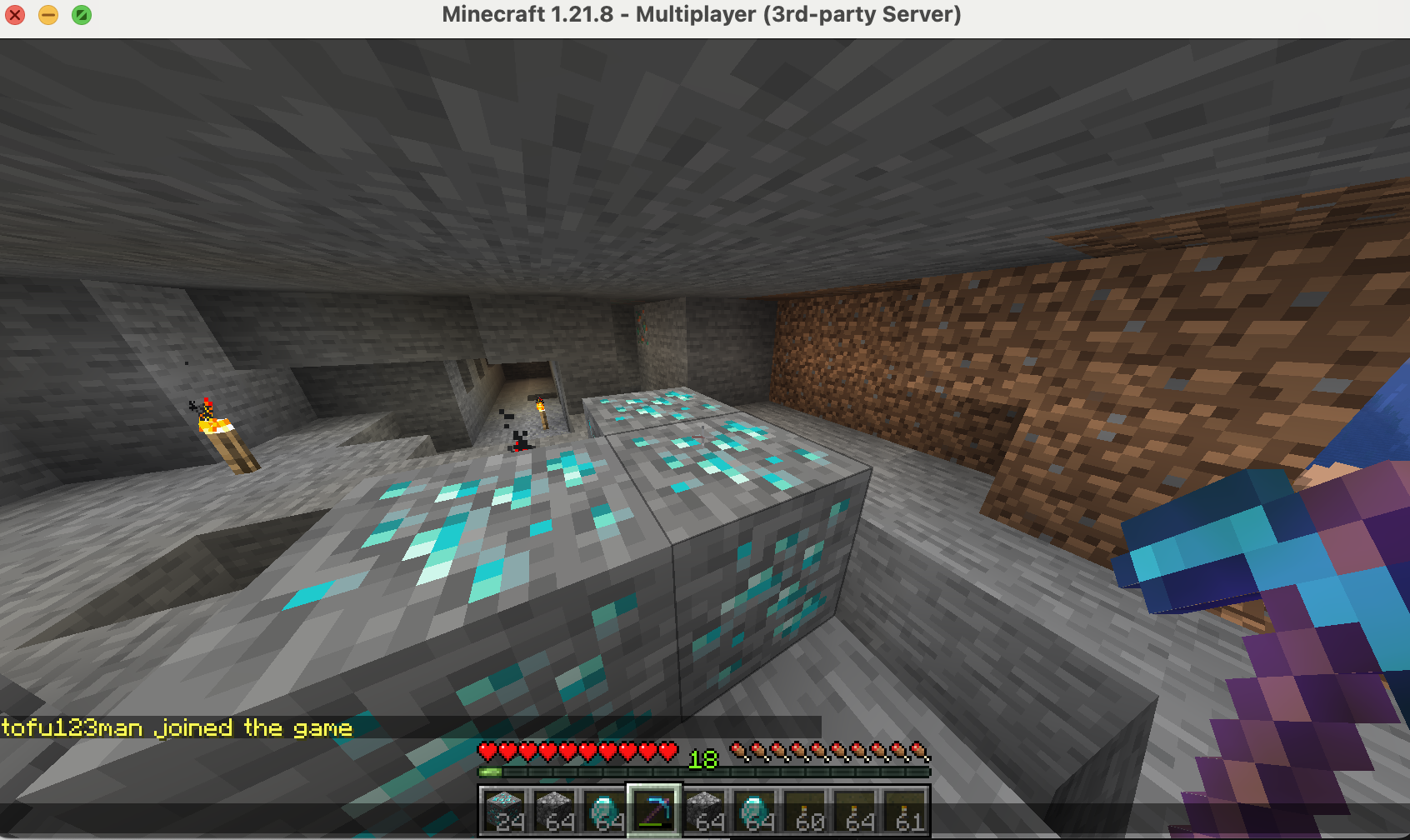
Join server and generate X‑ray behavior
Enter the world and intentionally simulate suspicious mining to validate detections.
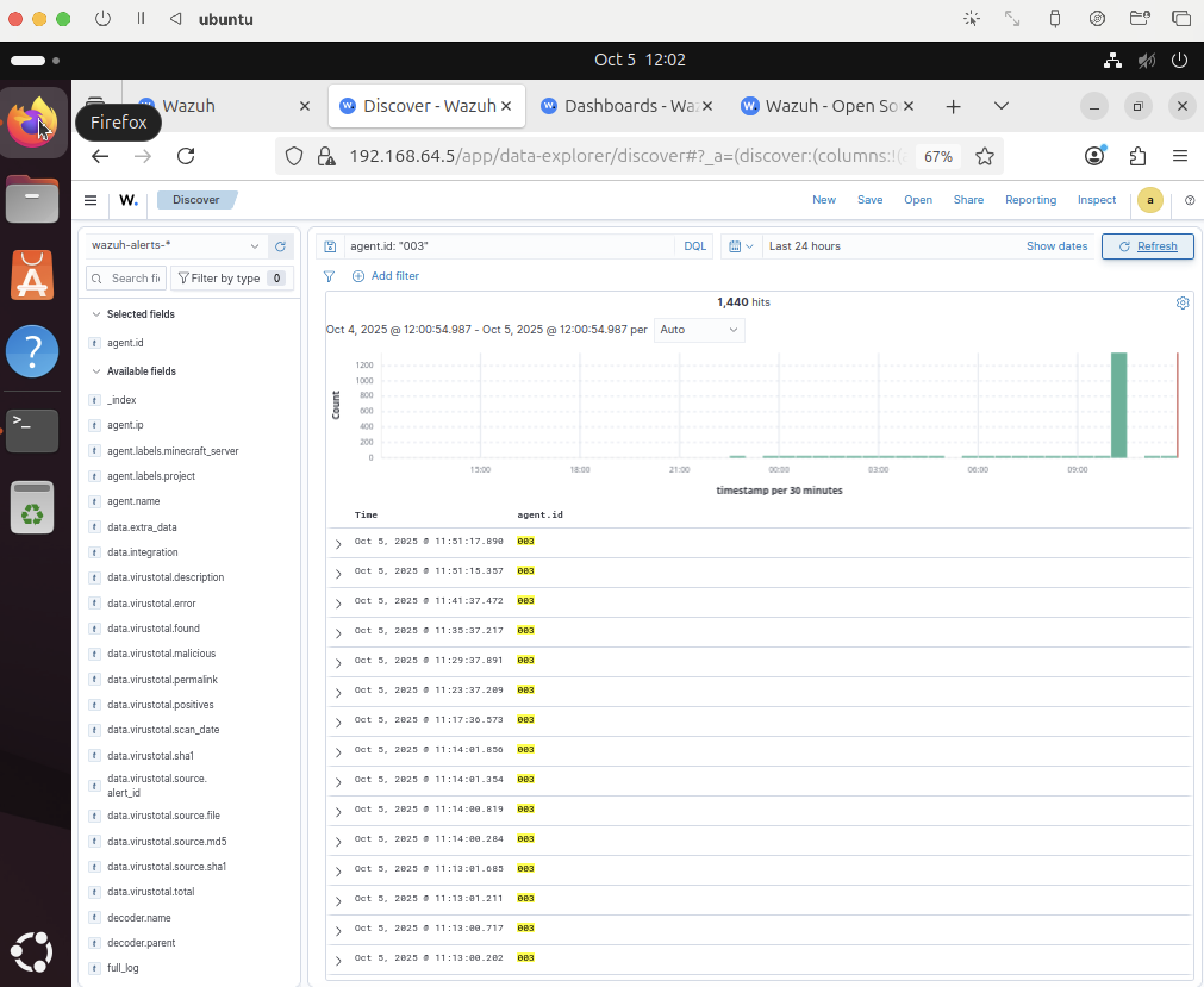
Confirm alerts in Wazuh
Observe alerts flowing into Wazuh—initially unstructured for gameplay analytics use‑cases.
Normalize fields for dashboarding
Adjust mappings (e.g., cast suspicion score to an integer) to make metrics aggregable and sortable.
Create multiplayer‑friendly visualizations
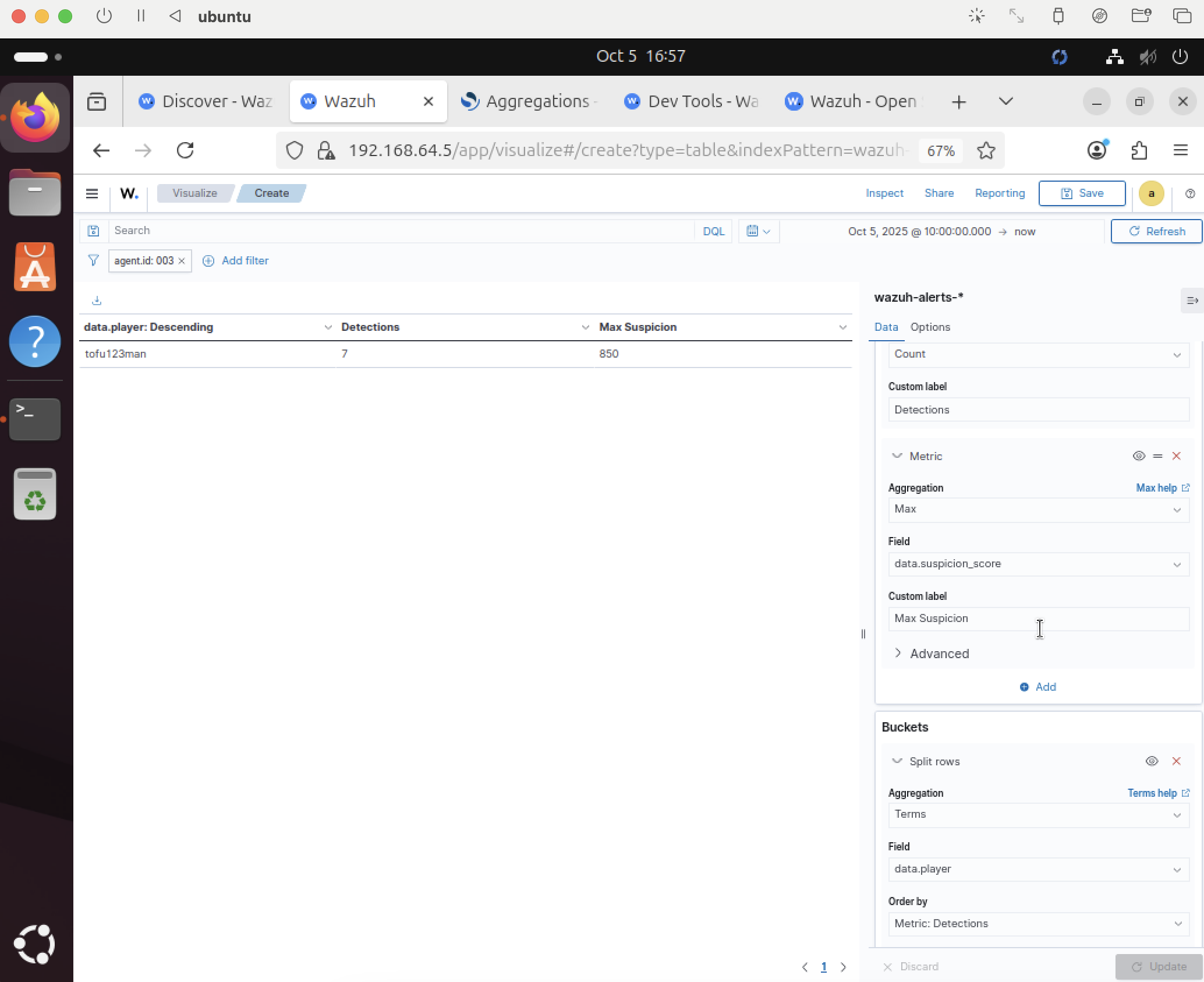
Design views by player, time window, and severity to track behavior across a live server.
Trend X‑ray detections over time
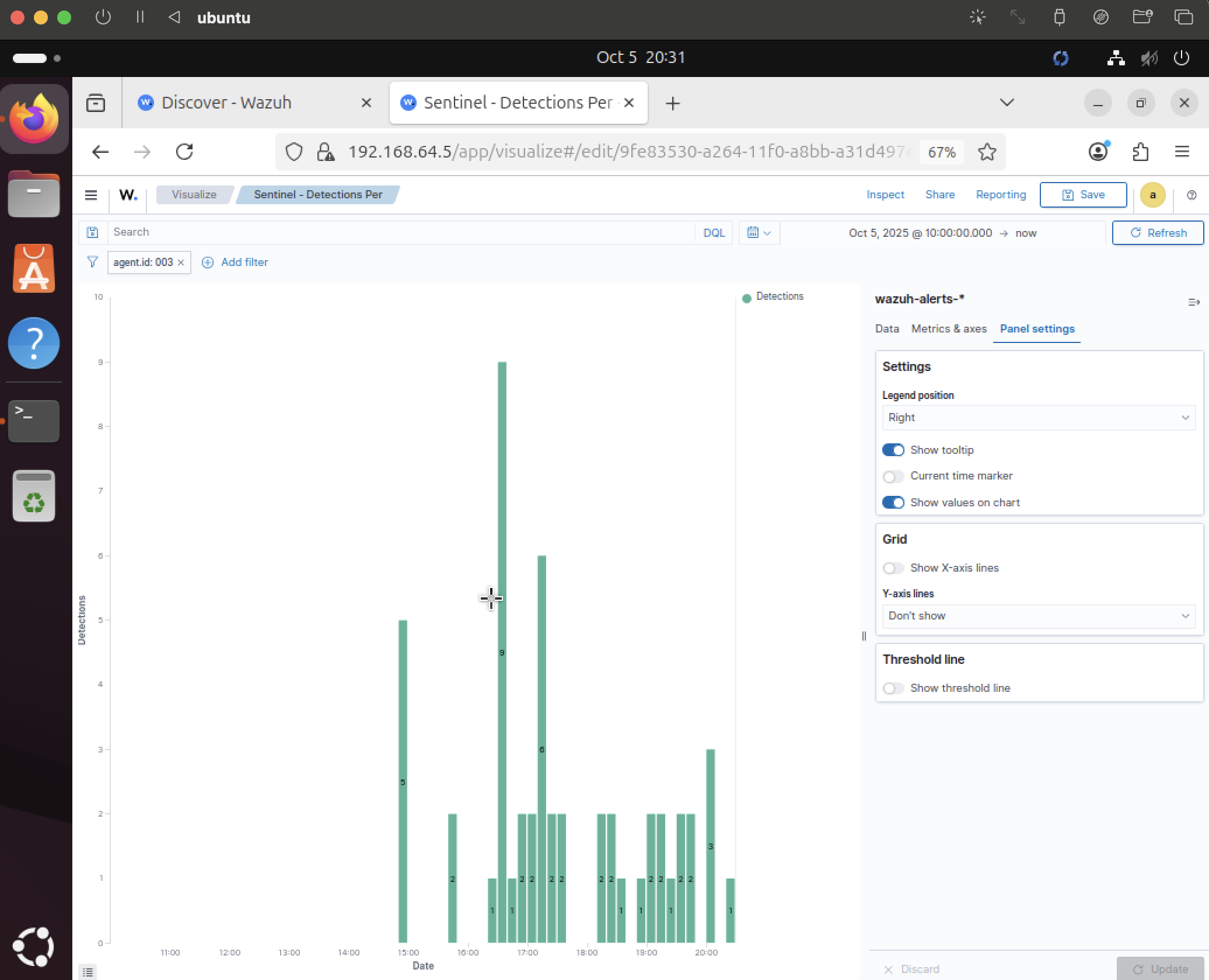
Add a time series panel to chart total detections by interval for easy spotting of spikes.
Assemble a focused dashboard
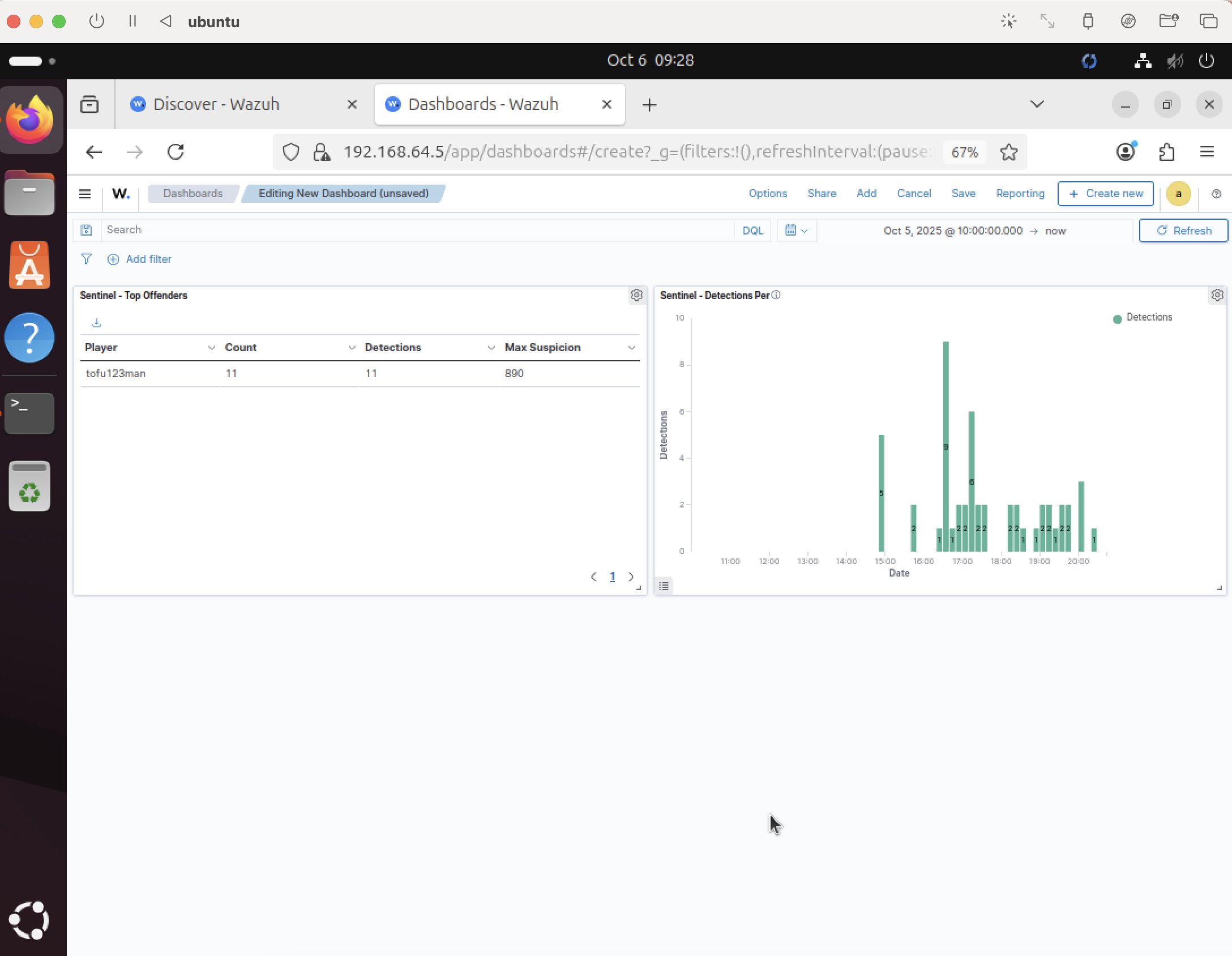
Combine the visualizations into a single, simple dashboard purpose‑built for gameplay oversight.