Lab Summary
This lab demonstrates the complete setup of automated malware detection and removal using Wazuh SIEM integrated with VirusTotal API. The system monitors file integrity, detects malicious files using VirusTotal scanning, and automatically removes threats through active response scripts. This creates a robust defense mechanism that can identify and eliminate malware in real-time without manual intervention.
VirusTotal API Setup
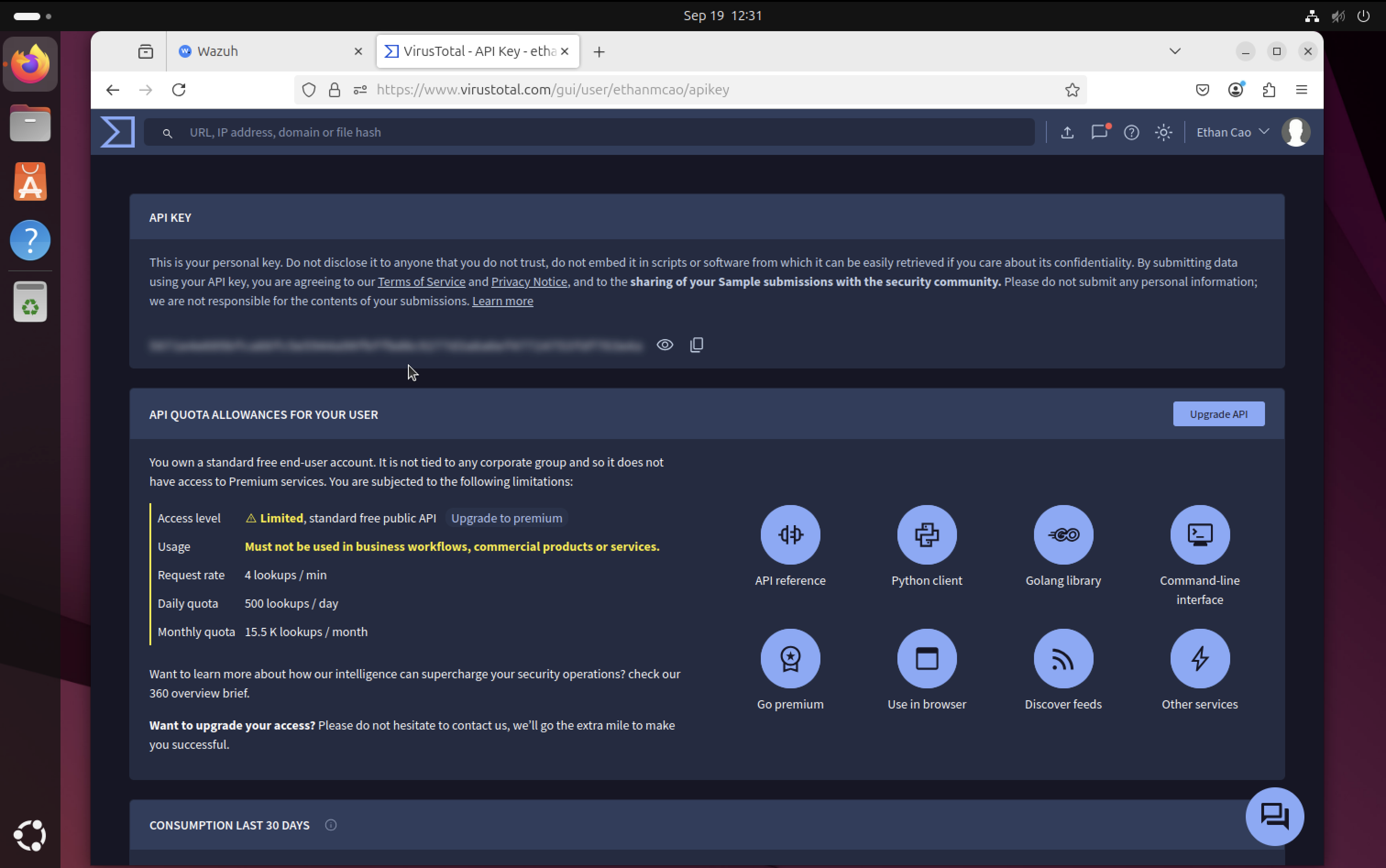
Signed up for VirusTotal account and obtained API key required for the automated response script. This API key will be used by Wazuh to scan suspicious files and determine if they are malicious.
Creating Test File
Created a test file on the Ubuntu host. This step is necessary to configure File Integrity Monitoring (FIM) on the Wazuh Agent, which will track changes to files in the monitored directories.
FIM Configuration Script
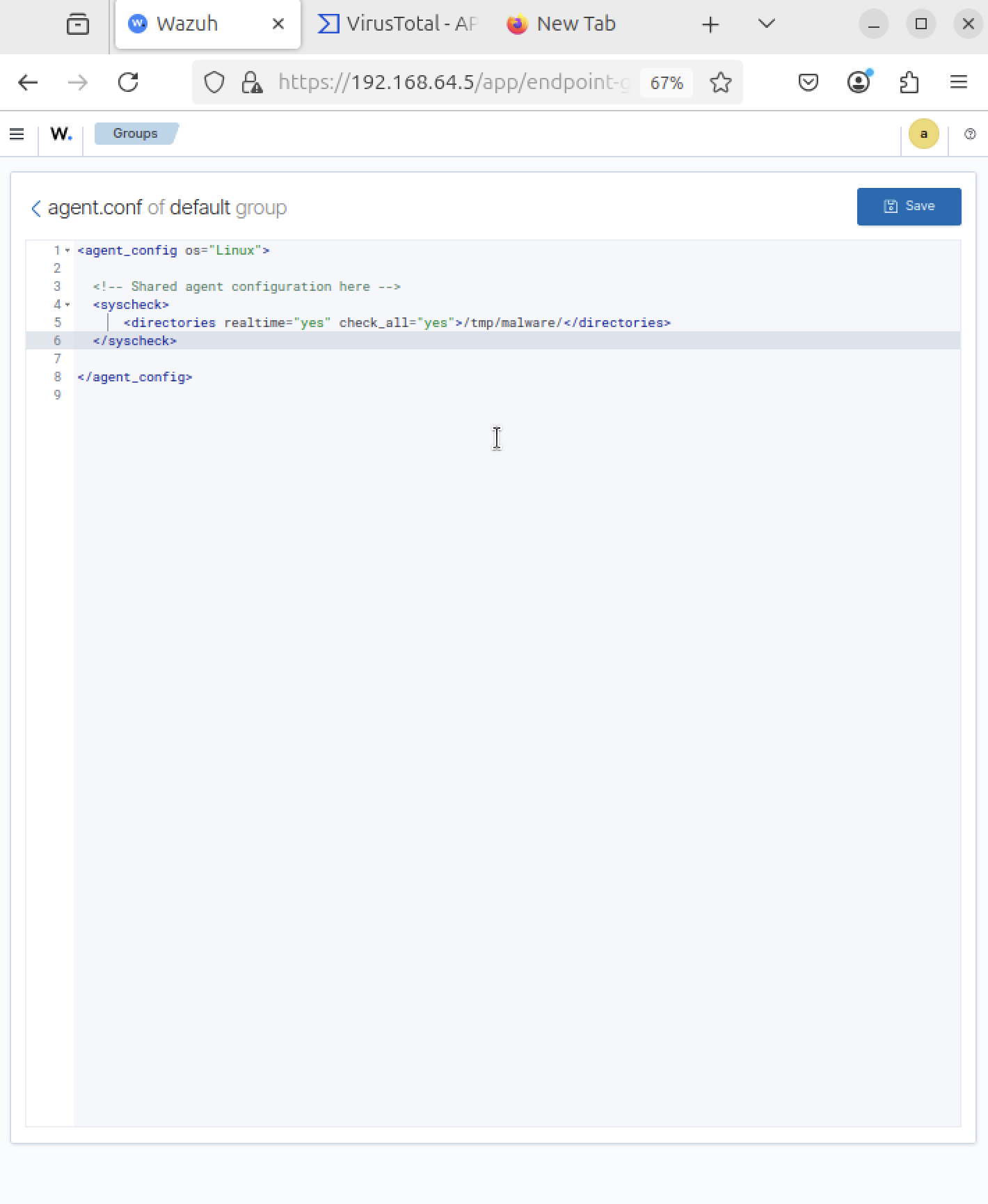
Configured the script on the Ubuntu agent to enable File Integrity Monitoring (FIM). This script checks for file integrity monitoring and ensures the agent can detect when files are created, modified, or deleted in monitored directories.
Agent Restart
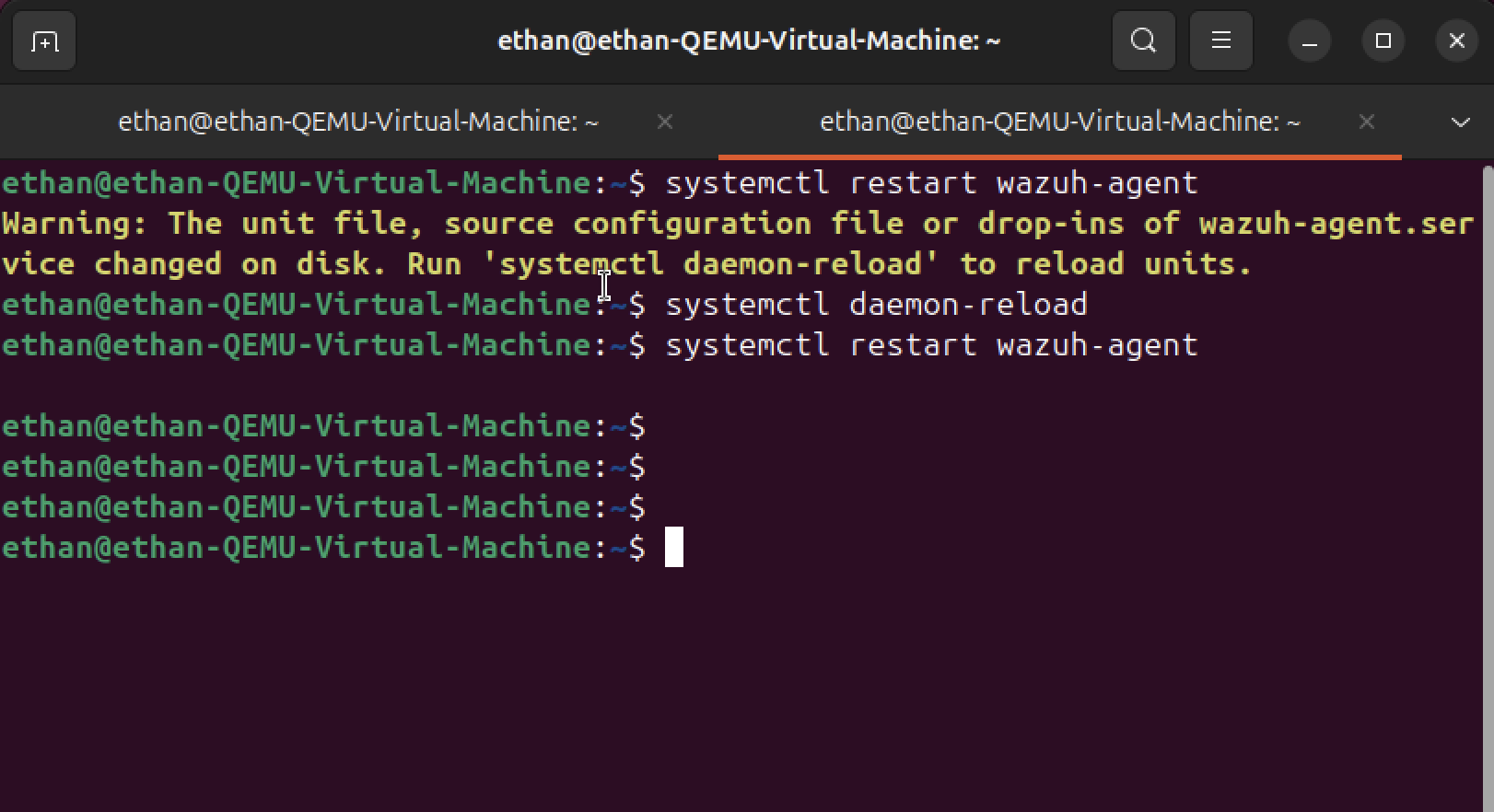
Restarted the Wazuh agent to apply the new File Integrity Monitoring configuration. This ensures that the FIM settings take effect and the agent begins monitoring the specified directories for file changes.
FIM Test File

Created a test file using `echo test.txt` to verify that the File Integrity Monitoring system is working correctly. This test file will trigger FIM events that should be visible in the Wazuh SIEM dashboard.
FIM Recent Events
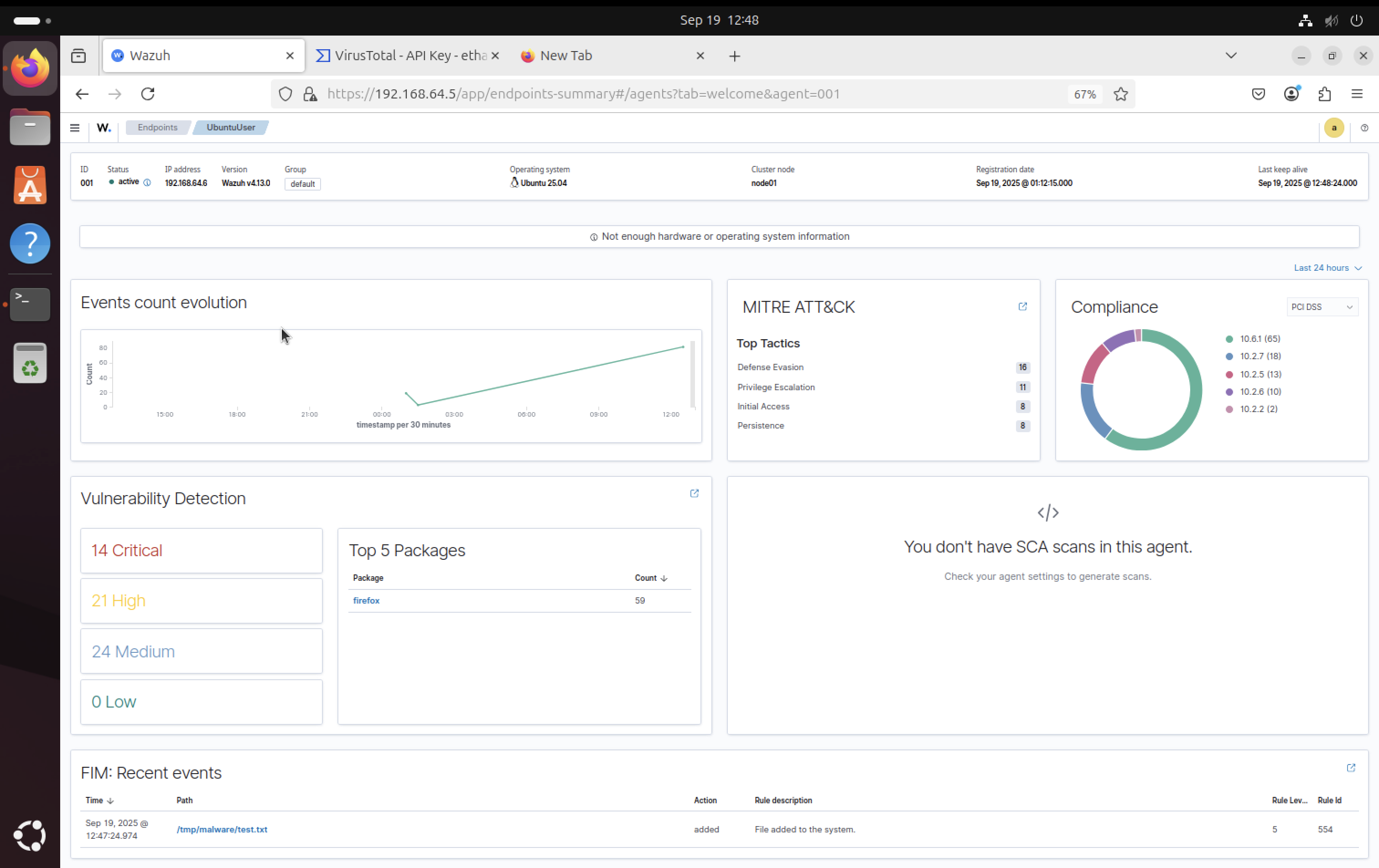
Immediately after creating the test file, we can see FIM recent events in the Wazuh dashboard. This confirms that the File Integrity Monitoring system is successfully detecting file changes in real-time.
FIM Events in Wazuh
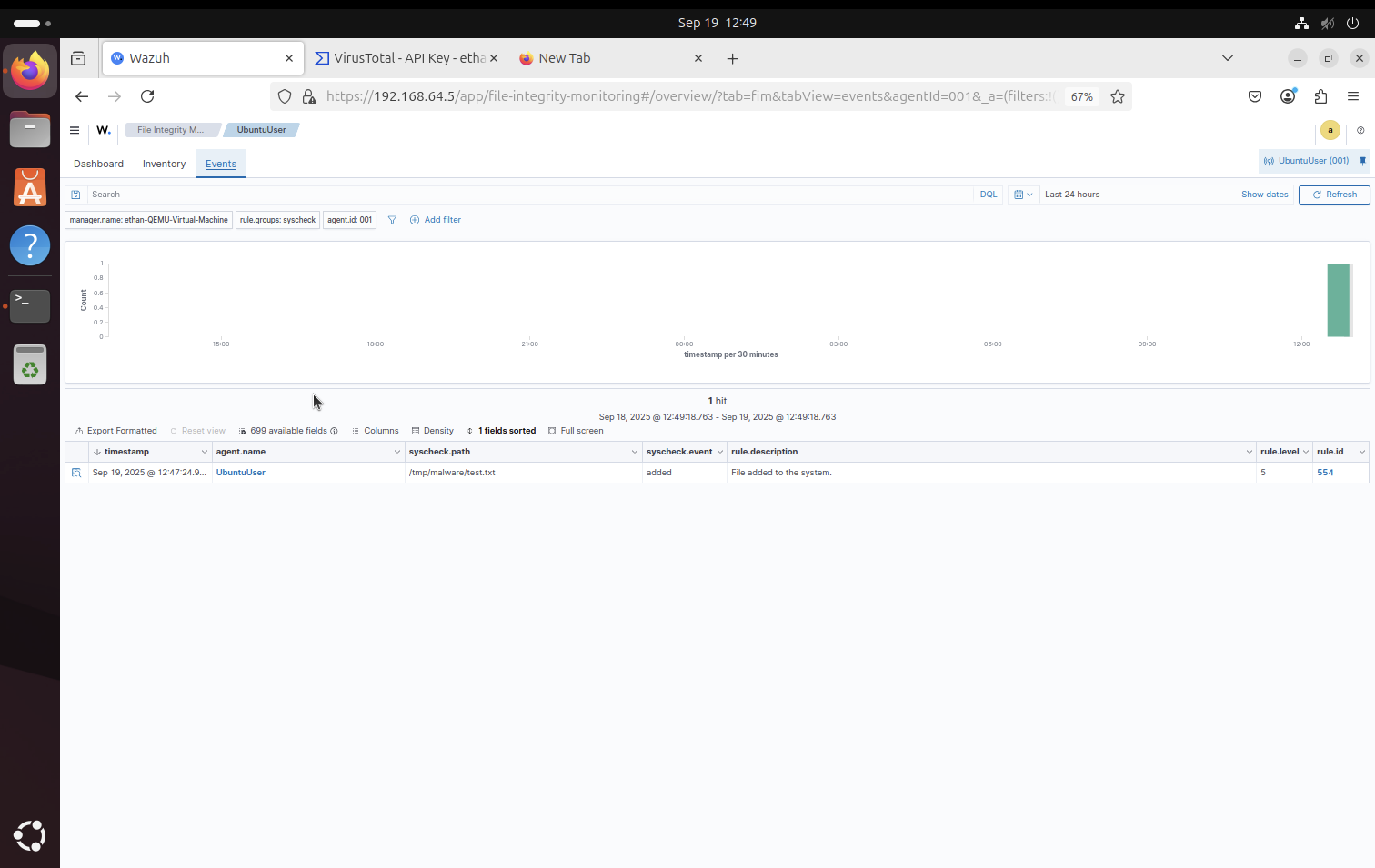
The file creation event is also visible in the main events section of the Wazuh SIEM dashboard. This shows the comprehensive logging and monitoring capabilities of the system.
VirusTotal Integration
Added the VirusTotal API key to the Wazuh server configuration on the Ubuntu SIEM server. This enables the system to automatically scan suspicious files using VirusTotal's extensive malware database.
EICAR Test Malware
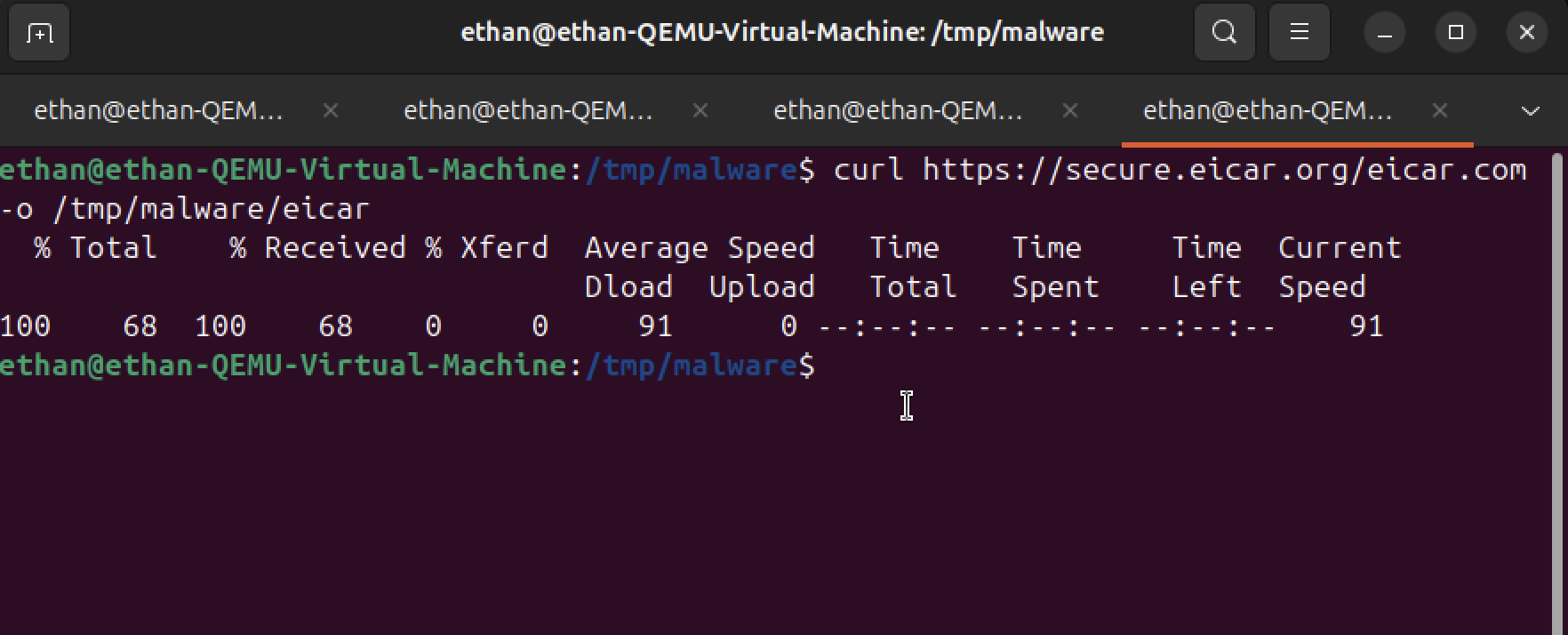
Downloaded the EICAR test malware file onto the user machine. EICAR is a harmless test file designed specifically for testing antivirus and security systems without posing any real threat.
Virus Detection Alert
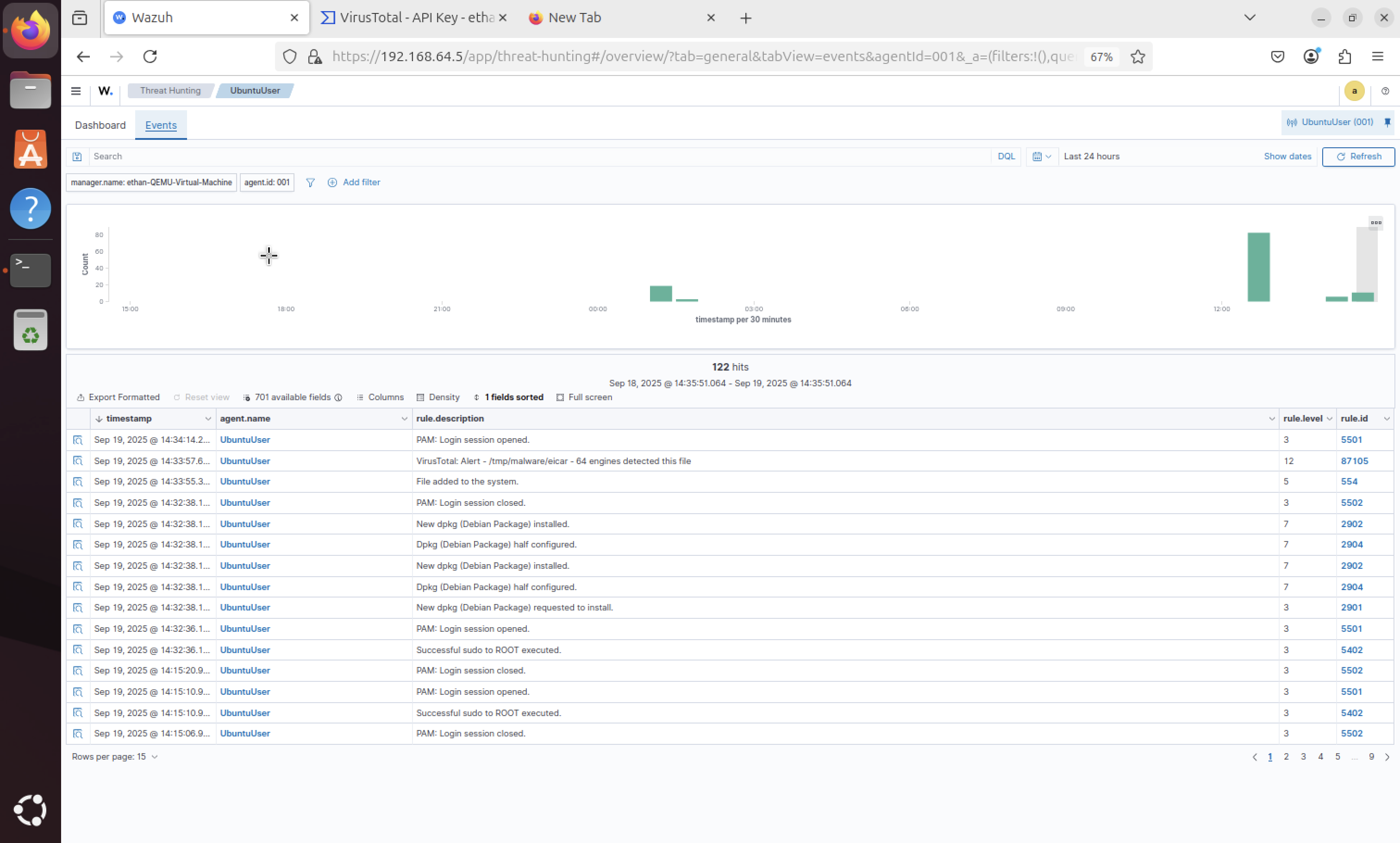
The Wazuh SIEM successfully detected the EICAR virus file and generated an alert. This demonstrates the real-time malware detection capabilities of the system integrated with VirusTotal scanning.
Virus Details
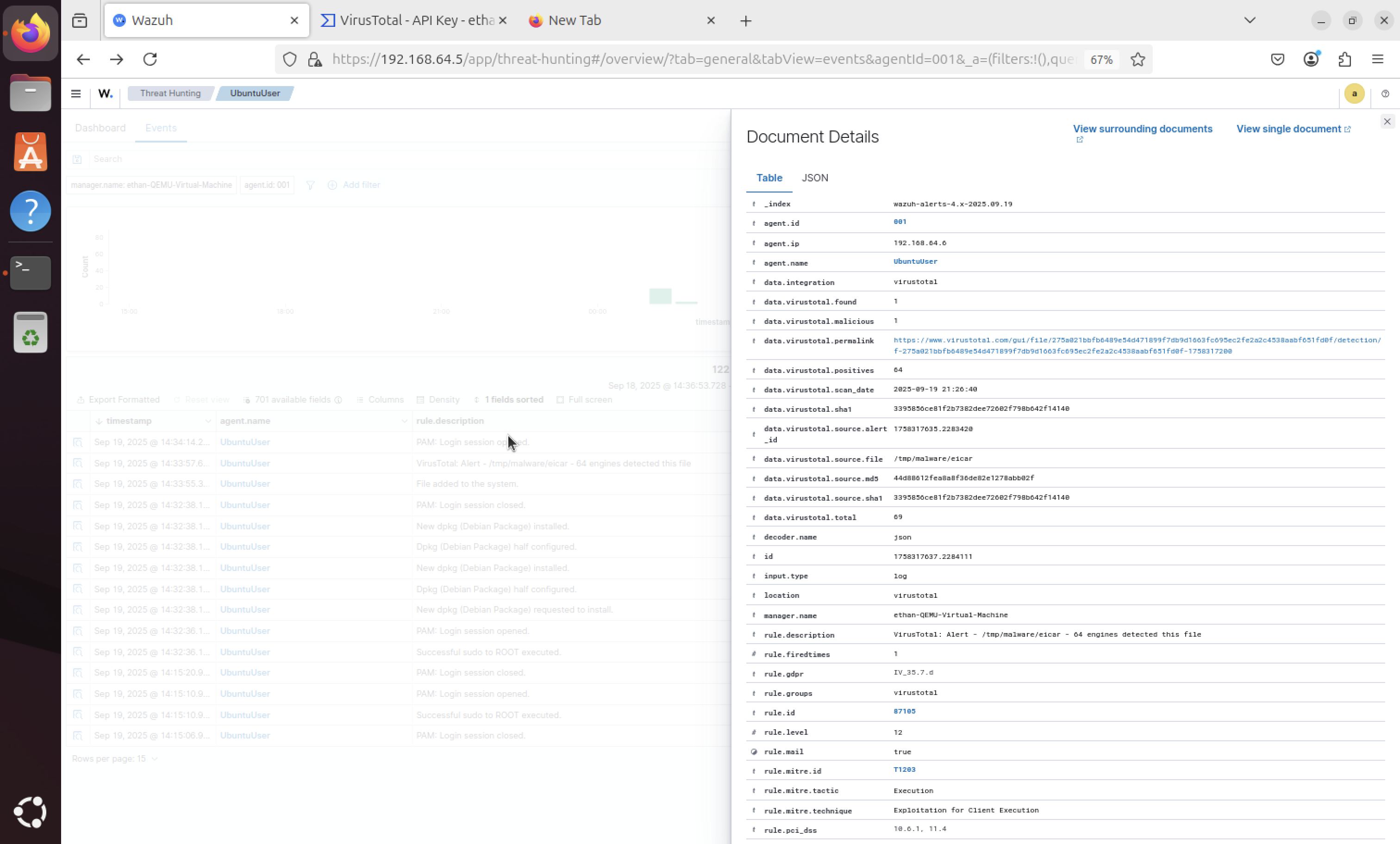
Detailed information about the detected virus is displayed, including threat classification, detection methods, and severity levels. This provides security analysts with comprehensive threat intelligence.
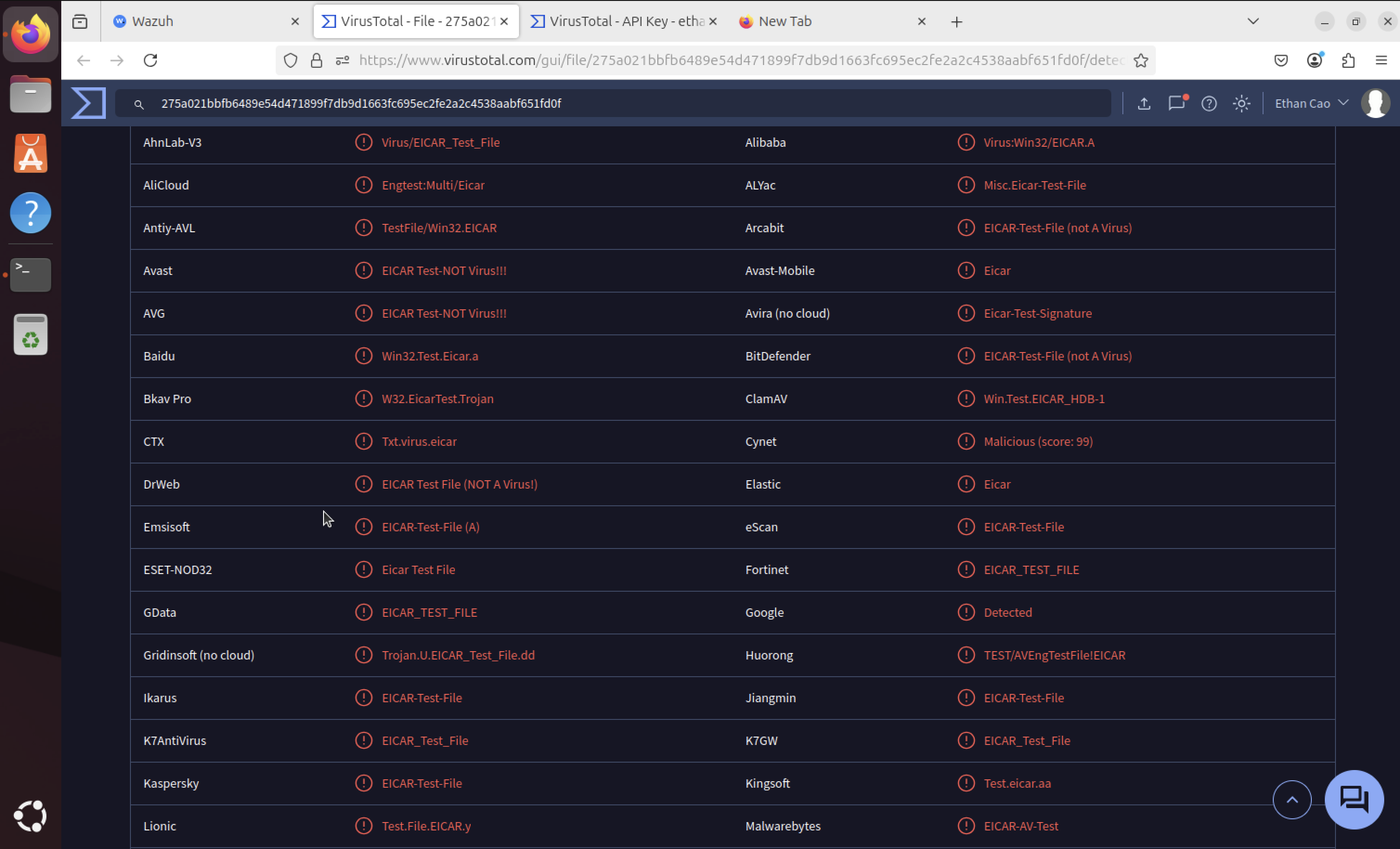
Multiple Virus Detections
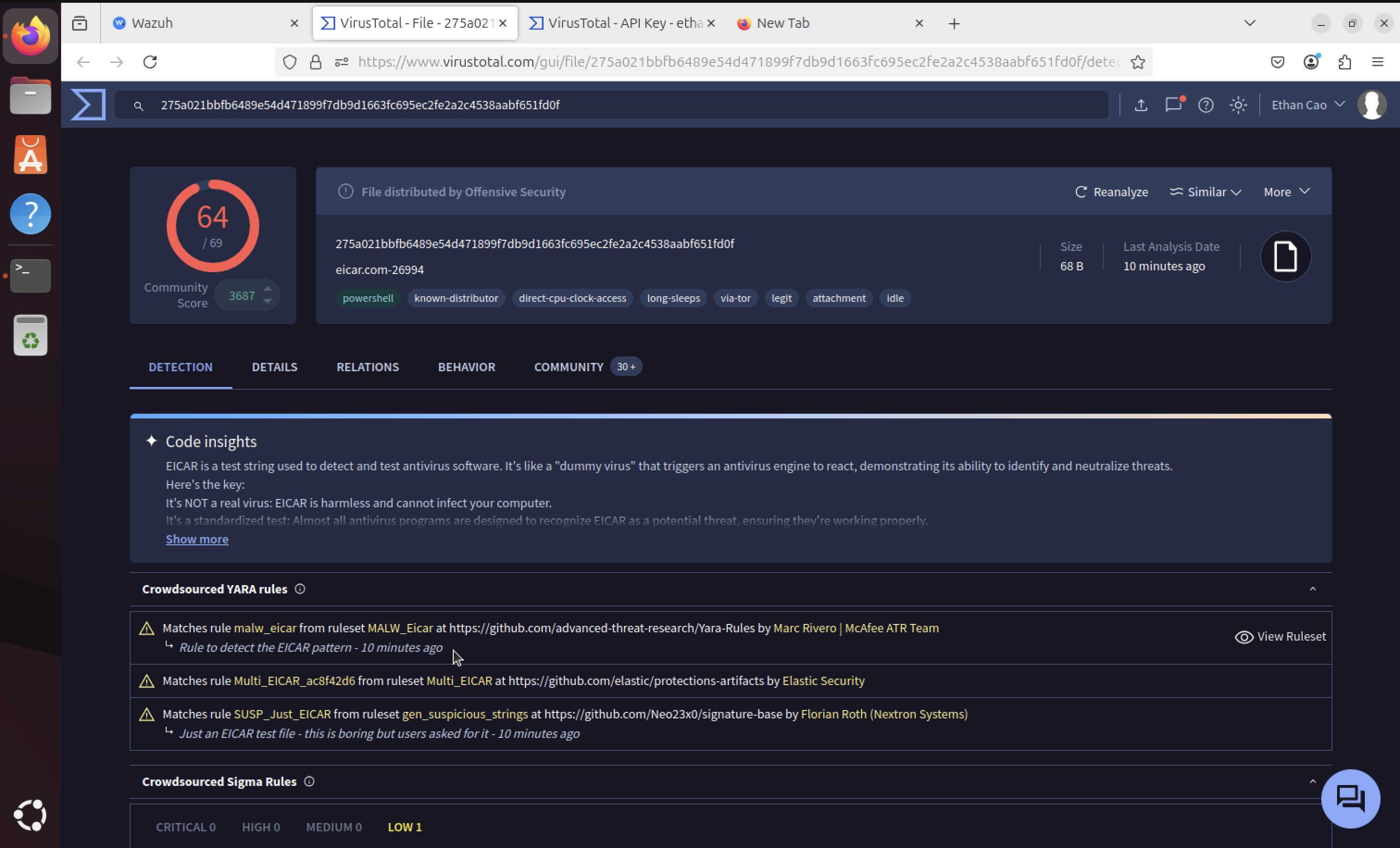
Clicking on the VirusTotal link reveals multiple virus detections and additional threat intelligence. Scrolling down shows more detailed information leading to the specific EICAR file detection.
Rule ID Extraction
Extracted the specific rule ID for the malware detection script. This rule ID will be used to trigger the automated response script when similar threats are detected in the future.
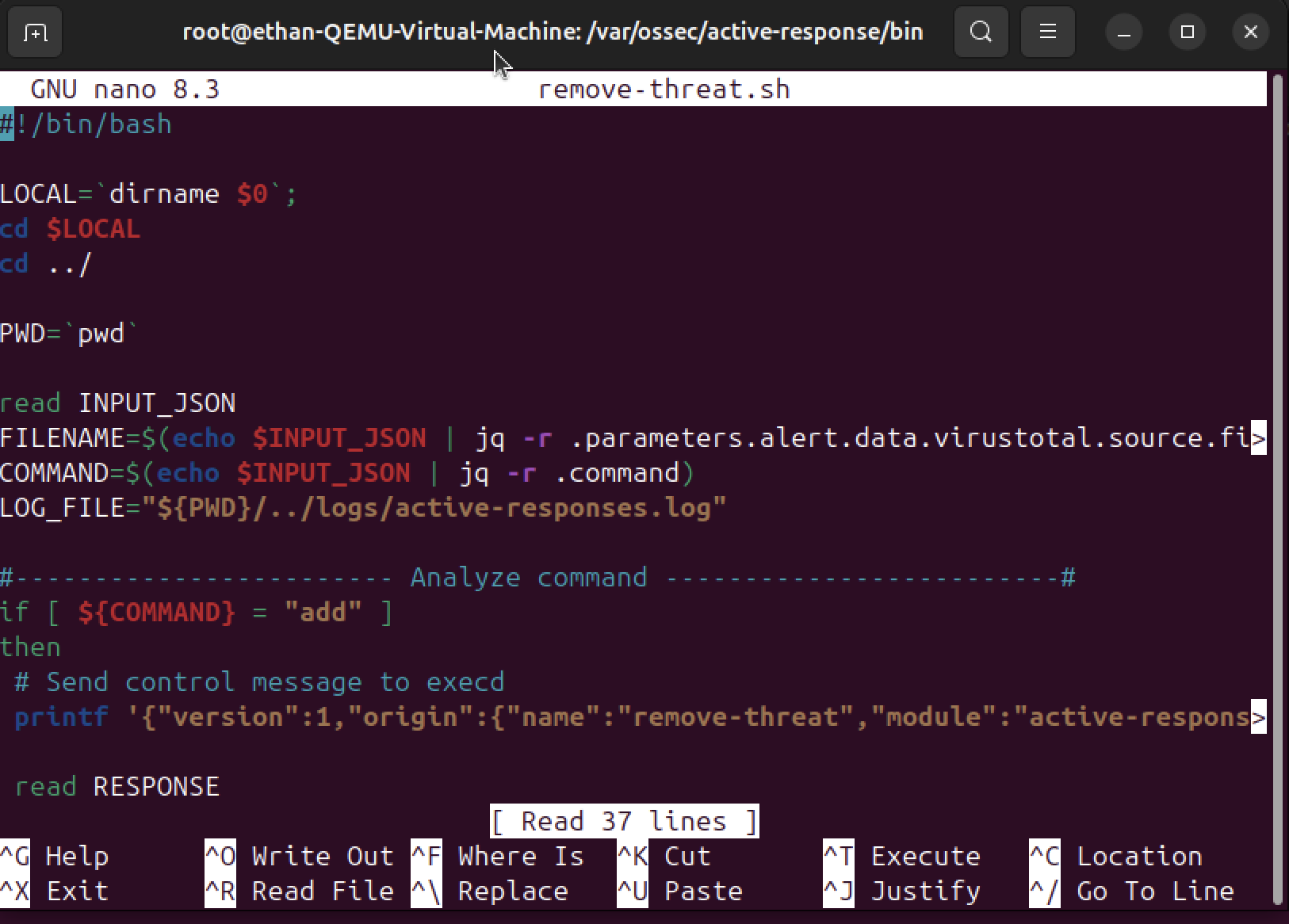
Malware Detection Script
Developed the automated malware detection and removal script. This script will be triggered when the system detects malicious files and will automatically remove them from the system.
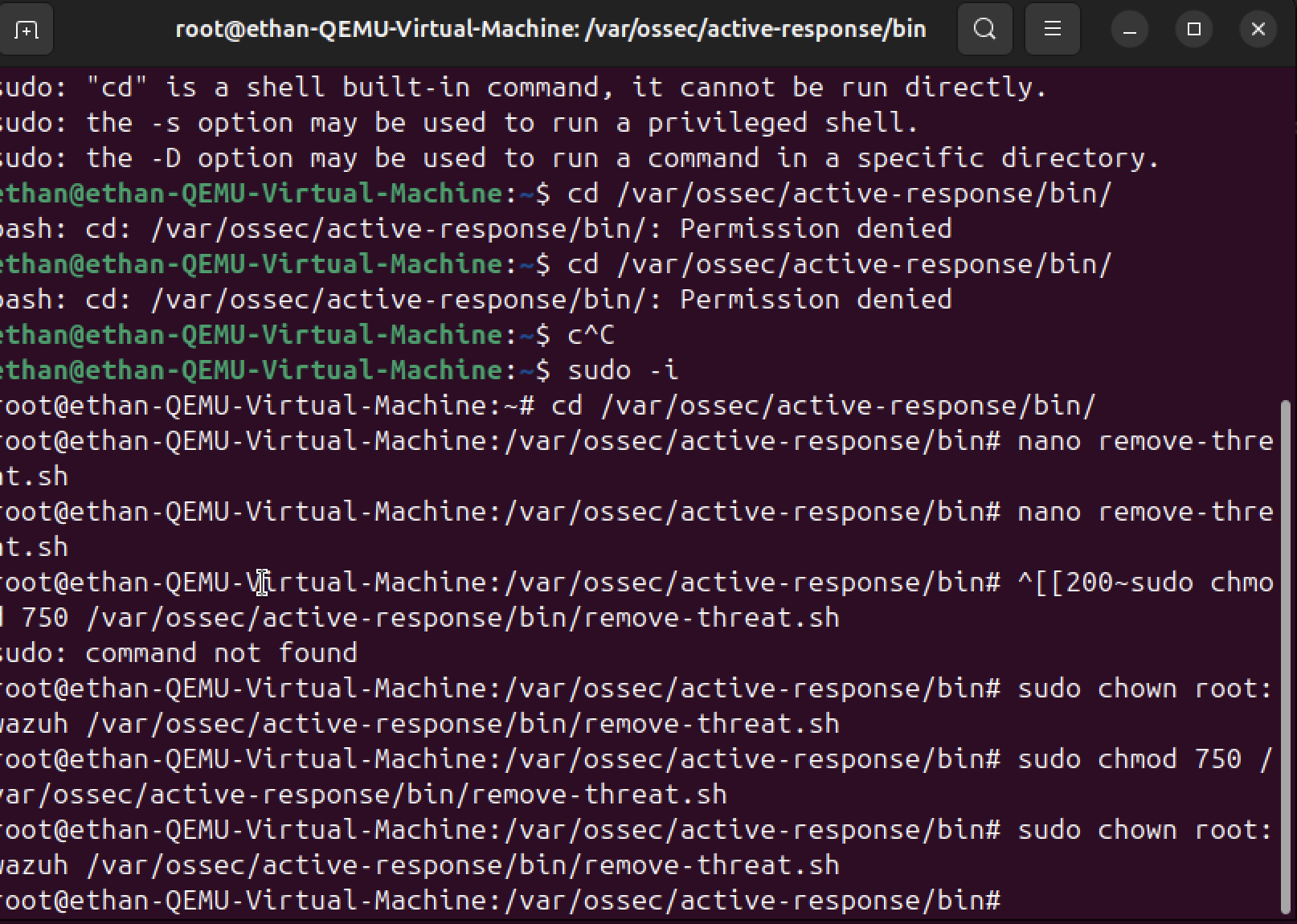
File Ownership Configuration
Configured file ownership permissions to ensure the automated response script has the necessary privileges to remove malicious files from the system without manual intervention.
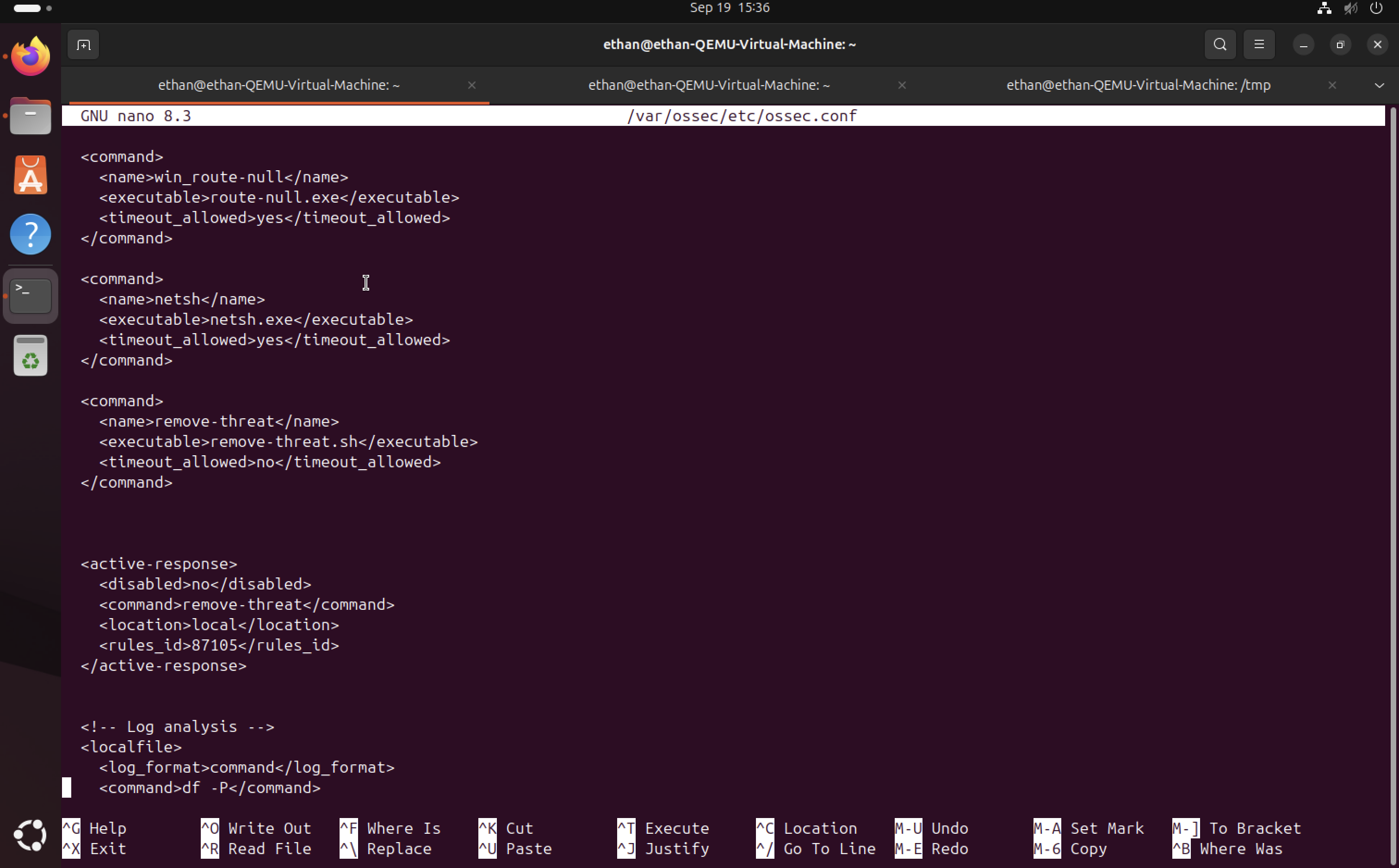
Active Response Configuration
Added the active response configuration with the specific port ID. This links the detection rule to the automated response script, enabling real-time threat remediation.
Clean Slate Test
Removed the original EICAR file to create a clean testing environment. This ensures that any future detections are from fresh downloads, allowing us to verify the automated removal system.
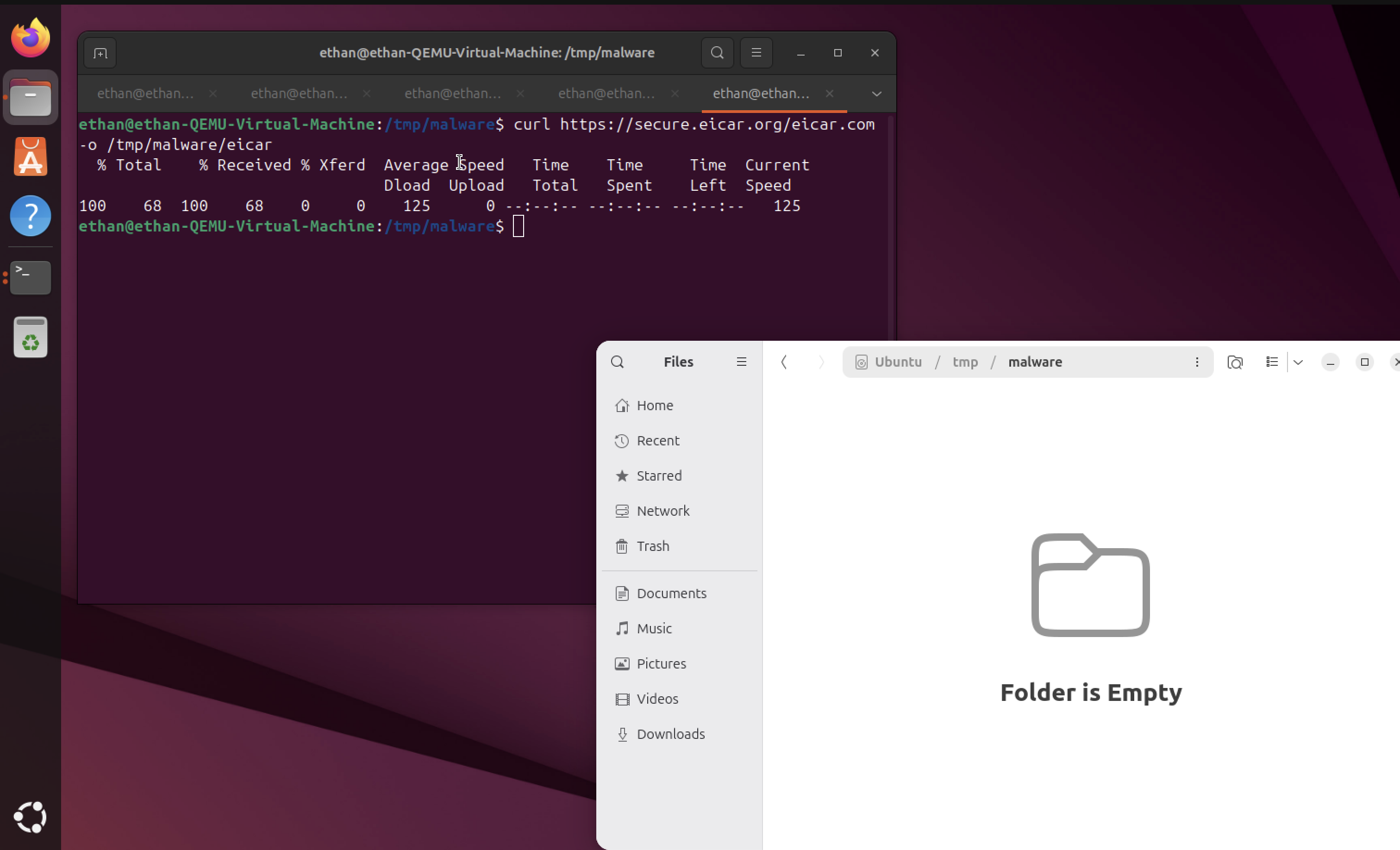
Automated Removal Test
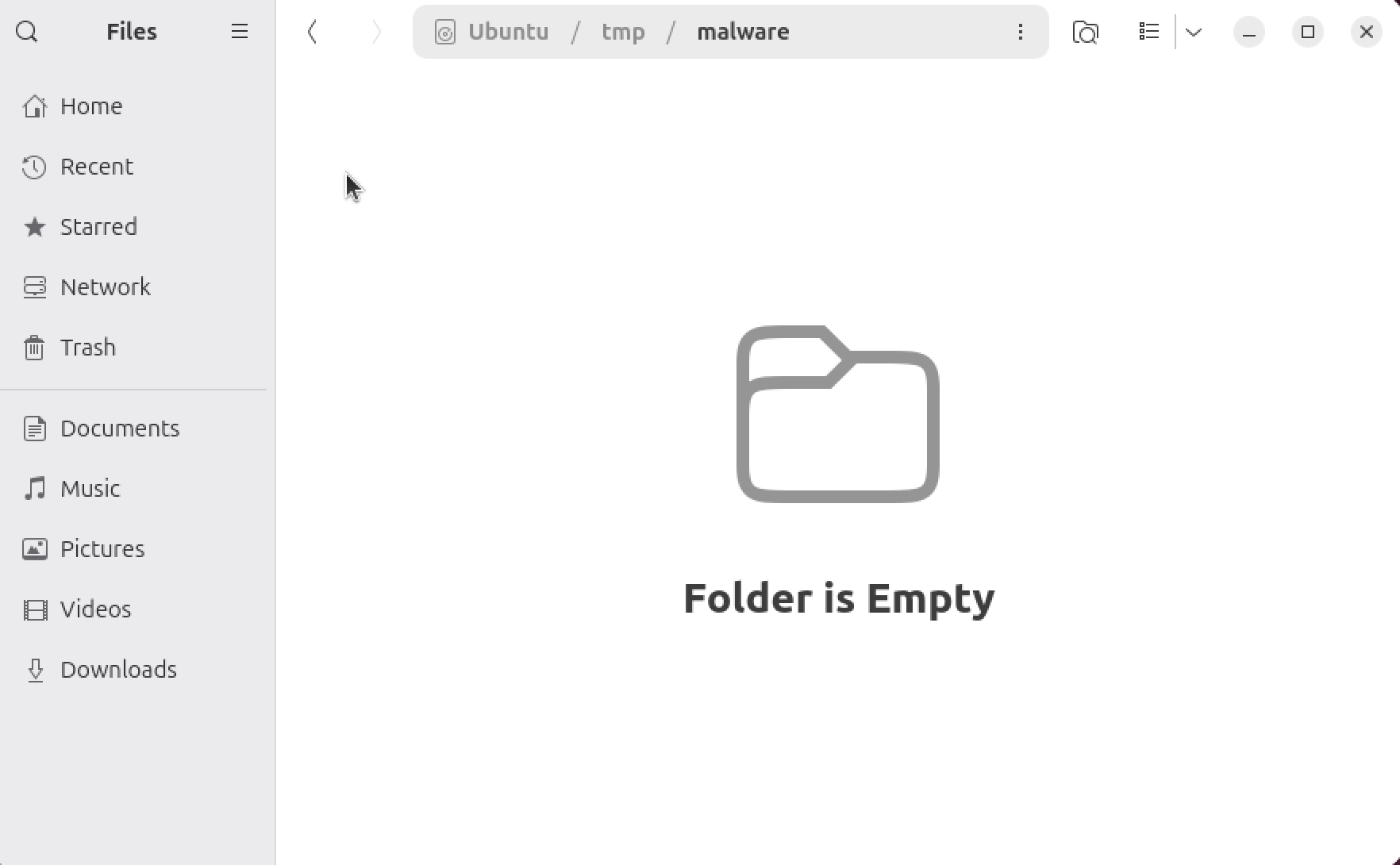
Downloaded the EICAR virus file again to test the automated removal system. Now when malware is detected, it will be automatically removed from the system without manual intervention.
Active Response Logs
In the threat hunting section of the Wazuh SIEM, we can see both the virus alert and the active response triggered in the logs. This provides complete visibility into the detection and remediation process.
Removal Confirmation
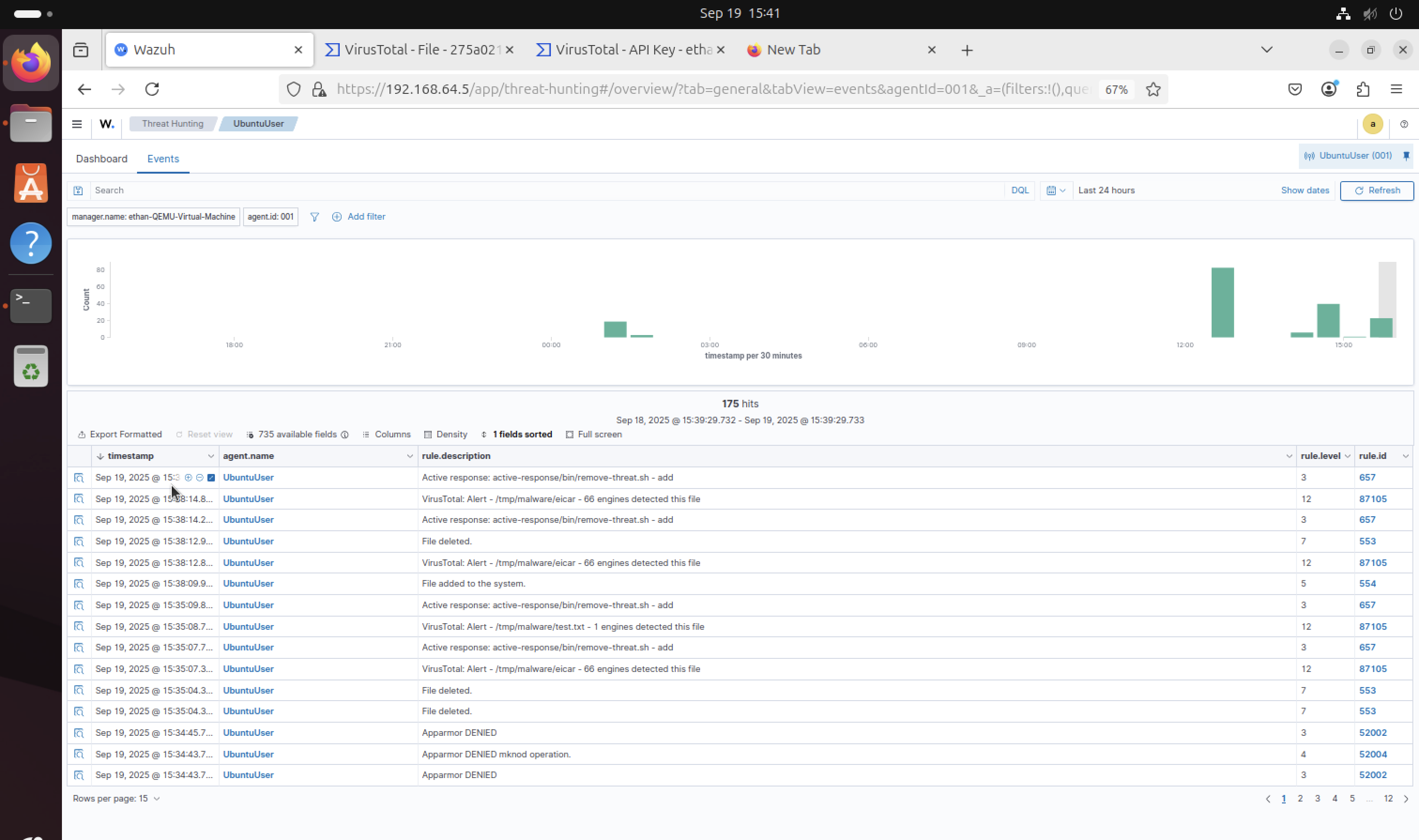
The SIEM logs show detailed data confirming that the malicious file was successfully removed from the system. This demonstrates the complete automated threat detection and removal workflow in action.